Extending our continuous integration (CI) work, that you can read about in previous blogs (IDS 2020.1 and IDS 2020.2), we have added automated updating for our core components and third-party dependencies to remove known CVEs. Using an open-source universal dependency update tool combined with our continuous vulnerability scans, we are able to systematically and automatically make sure that the software is up-to-date and with as few vulnerabilities as possible.
Ubisecure Identity Server utilises a number of external components; Java, PostgreSQL, Tomcat, WildFly, amongst others. For example, within previous releases we have supported the use of PostgreSQL 9.6, used as a datastore for our Accounting Service and CustomerID portions of the Identity Platform. As PostgreSQL 9.6 is nearing its end of support, see PostgreSQL Versioning; we have updated our deployment testing to utilise PostgreSQL 12. For new installations, we now support using this long-term supported version of PostgreSQL. For existing installations, we will be testing and updating instructions to assist your move from 9.6 to 12.5 during the first half of 2021. The System recommendations and supported platforms page has been updated to include new supported versions and which upgrade paths we have tested.
Ubisecure started the implementation of OpenID Connect in 2015 with Mobile Connect and has completed regular improvements each year to make sure that we are following the specifications laid out by the OpenID Foundation. In this development cycle we have started the self-certification for OpenID Connect Basic Profile. While we are compliant with all the common uses of OIDC, there are a few edge cases that need to be adjusted (response error codes, for example) to be fully compliant for self-certification of the OIDC basic test suite. We will be updating those minor deviations in the next release cycle. Similarly, the finalised specification for CIBA Core 1.0 has been reviewed during this development cycle and will require just a few modifications in the next release cycle. Completing the standard CIBA Core 1.0 specification will permit any developer to create their own CIBA integration to our Identity Platform. If you are considering utilising a Backchannel Authenticator please review the CIBA specification to be ready to implement it later this year.
New in this release
Proof Key for Code Exchange (PKCE) for OAuth 2.0
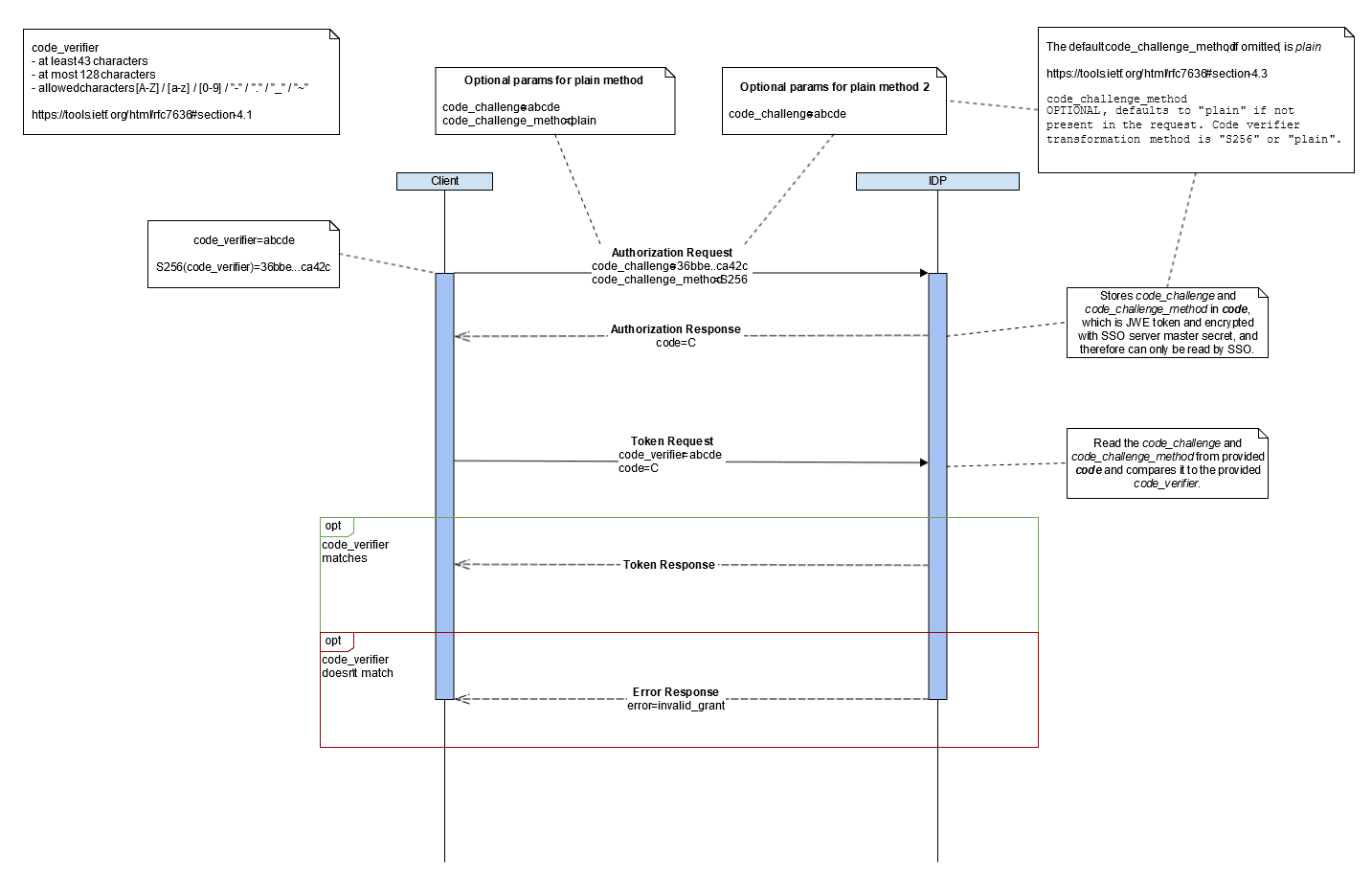
One of the new features within this release is the support of Proof Key for Code Exchange (PKCE). PKCE is an extension to the Authorisation code flow to prevent authorisation code interception attacks. Starting with SSO 8.7.0, the Identity Platform will check if a code_challenge and code_challenge_method is sent with the Authorisation Request and validate it against the code_verifier sent along the Token Request. The code_challenge_methods_supported are “plain” and “S256”. This initial implementation is supporting SSO as an OpenID Provider (OP), which means that if you already have a client using PKCE towards SSO, by updating to SSO 8.7.0 the previously ignored values will start to be validated. To enforce the use of PKCE by your clients see information about Client configuration reference – SSO.
CustomerID REST API with SSO OAuth2 Access Tokens
With the latest version IDS 2021.1, Administrators of SSO are able to configure users or groups that have access to the CustomerID REST API. This will give you better security and an overview of who is using the APIs and when have they been used. Administrators of CustomerID are also able to disable the earlier used HTTP Basic authentication scheme (username and password) to ensure that the old way of calling the APIs is not used anymore. Moving forward in 2021, we will introduce access control (RBAC) to allow sharing access to CustomerID APIs, not only within your company, but to your customers and partners as well.
Lifecycle Management
We have focused on updating external components and third-party dependencies in our main components – SSO, CustomerID and Accounting. For example, the external components Tomcat and Wildfly have both been updated. Tomcat has been updated to 9.0.41 and Wildfly has been updated to 21.0.2.Final. Together with the third-party library updates, many identified CVE’s have been removed. Security is a never-ending process, so updating to this latest release of Identity Platform will help to secure your environment. A full list of updated dependencies can be found from SSO 3rd party licenses and CustomerID 3rd party licenses.
For a full list of features, improvement and corrections, please see https://developer.ubisecure.com/docs/display/IDS20211/Identity+Server+2021.1+Release+Notes
Head over to https://www.ubisecure.com/developers/ to download the latest version of Ubisecure Identity Server today!



About The Author: John Jellema
As VP Product Management, John is responsible for ensuring Ubisecure’s ongoing development of its Identity Platform, optimising the feature development while driving generational change across the IAM delivery platform. Since joining Ubisecure in 2017, John has refocused the cloud and on-premises delivered services to fulfil customer expectations across the Nordics.
Prior to joining Ubisecure, John worked for Verizon as a Global Security Product Manager, developing and managing its DDoS platform around the world. With more than 20 years experience in global product management, John is passionate about seamless technology integration. Standing on the shoulders of giants permits us to achieve greatness today and into the future.
More posts by John Jellema