When delivering online services to your customers, there are two terms that come up quite often that might require some explanation through comparison. Single Sign-On and Step-up authentication are technologies to help your customers navigate your applications. Visually, Single Sign-On vs Step-up authentication is lateral vs vertical movement.
Lateral movement
Once your customer has authenticated to your application through your identity provider component, a session is created and the information stored into the browser memory. This same session information is stored within the identity provider and usually it has an expiration date (or hour). A typical session length is one hour, and in financial applications the session length is often shorter, normally 15 minutes. The authenticated session is the vehicle that provides the capability to Single Sign-On (SSO) to other applications from the first application; this is how SAML single sign-on works. The session information stored in the browser (and the identity provider) will tell the next application that the user has been authenticated, and everything is ok.
With more recent protocols the important item is called a token. When a customer has been successfully authenticated, a token is issued and this same token is then used across connected services providing single sign-on from one service (resource in OAuth speak) to another. The job of the Identity Provider is to handle the session creation, token issuance and verification transparently, so that the user never has to realise that one application uses a SAML protocol and the other application uses OAuth. For the user, it just looks like they are breezing from one application to the next without any hiccups. The same applies to your IT admins, when setup correctly the Identity Provider will allow them to easily plug in applications and apps that can consume different types of protocols. For a longer and more technical explanation on the differences between SAML & OAuth, I recommend you read this excellent blog by Jesse.
The lateral movement from one application to another can happen as long as the receiving application requires the same level of assurance, or less, than the application the user is coming from. If the receiving application requires a higher level of assurance of the identity of the user, the lateral movement stops and the user hits the gatekeeper.
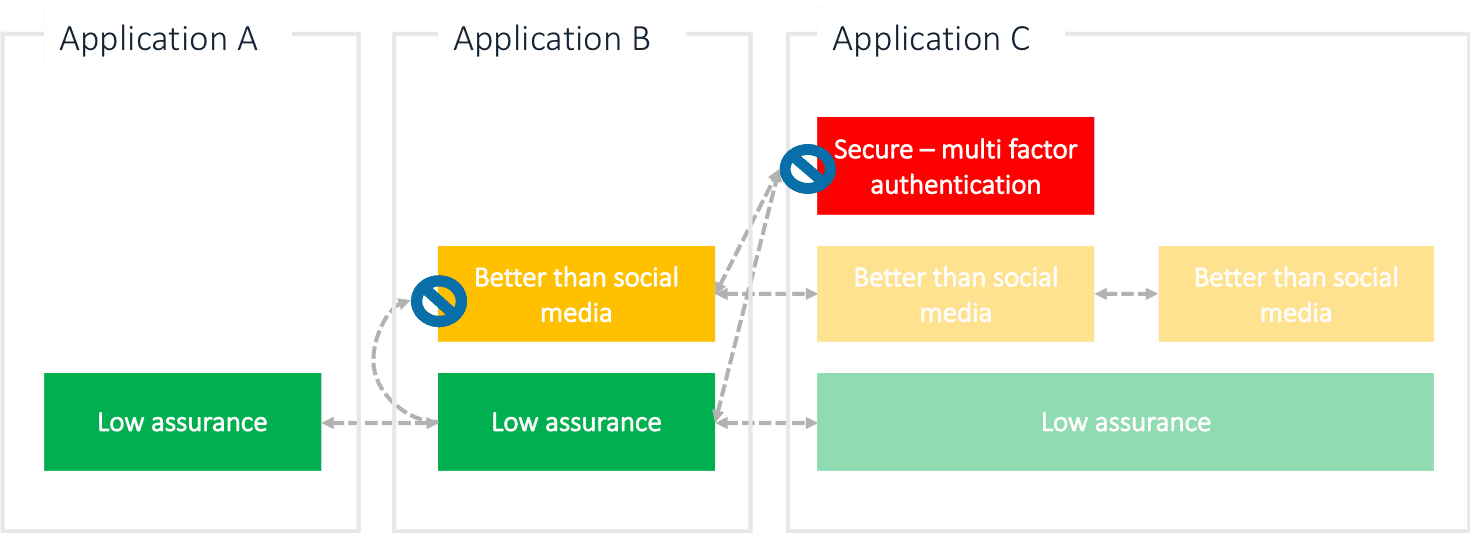
Vertical Movement
When a customer needs to access a more secure / confidential data, and they just used a social media account to access the application, step-up authentication occurs. You can visualize it by thinking that the user goes deeper into the application sensitive areas, and those areas are secured by sturdier gates than the entrance was. When the user takes this step vertically to a more secure area, it depends on the nature of the area which kind of step-up authentication must take place.
Classifying your data, or data that you store, is an important step to understand the demands for user identity verification. Different classes (of confidentiality) need appropriate protection mechanisms. Username + password is still, unfortunately, the most common method to enter online applications. Social media accounts fall into this category as well, in most cases anyways. What we are talking about is weak authentication where the identity (how reliably was the true identity of the user verified when created) and authentication (strength of the method) assurance levels are poor, or sometimes non-existent.
There are several public and international classifications for different digital identities and their related authentication methods. For a comprehensive look at online authentication, just download this whitepaper. In a nutshell, the more confidential the resource the user is trying to access, the stronger the identity and authentication method really should be. The good news is that these methods need not to be cumbersome nor inconvenient for the end user. Modern strong or multi-factor authentication methods using biometrics and a device are becoming more and more commonplace thanks to the proliferation of biometric sensors in e.g. mobile devices. But, please don’t even consider deploying a one-time-password generator devices to your customers if you can avoid it. You do know that in every household there exist a tiny black hole where these small devices vanish. It’s next to the single sock sucking black hole.
Single Sign-On vs Step-up authentication is about direction
There you have it. Single Sign-On vs Step-up authentication is about lateral, convenient movement between your deployed applications versus protecting he more sensitive areas with step-up authentication. And remember – you don’t have to demand the strongest of authentication to let your customers in, you have the option of using stronger authentication only where it is needed. The Identity Provider will take care of the details and will guard the more secure areas and demand proper authentication when a user tries to access them. So, if your organisation needs both single sign-on enabled for your customers and step-up authentication to protect secure areas, you (may) need an identity provider. Sure, you can acquire social media federation from an outsourced service (or build your own), and then bolt on one or more secure authentication methods, but chances are that if you have more than one application, this build-when-you-need process will become a mess. Let an Identity Provider work their magic and save a bunch of IT admin meltdowns and cash.
Now for the pitch part…
Ubisecure Identity Platform is one of the first European Kantara Initiative (back when it was called Liberty Alliance) full matrix interoperability certified Identity Provider products and we participate in the work of both Kantara Initiative and OpenID Foundation actively. If your organisation needs a solution for Single Sign-On and step-up authentication (and much, much more), look no further.
[button text=”Contact Us Now” url=”https://www.ubisecure.com/about/contact/” type=”info”][/button]



About The Author: Petteri Ihalainen
More posts by Petteri Ihalainen